#Web200
For this challenge, credentials were provided. We see the following page upon logging in:
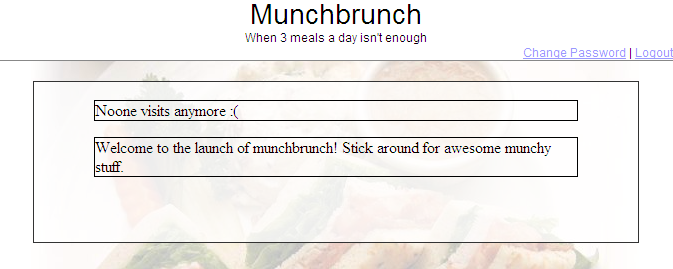
Clearly, this site doesn’t get many visitors
Nothing particularly stands out. To the source!
<iframe src="content/news.php?type=1"></iframe>
It seems the news content is loaded via an iframe from a php file. Our next step should be to check out this file.

We know that news.php accepts a field which probably determines what content is displayed. It’s probable that the content is being served from a database. Thus, we can play around with the type field to see if we can get a working query. Some SQLi we can try:
--
0 or 1 --
" or 1 --
Whenever we pass something to the code that isn’t valid or for a type with no news, we get a simple “No news” error. After a few tries it should occur to us that news.php may not be vulnerable. So the question is, what next?
What of the directory that news.php is sitting in? It’s plausible that the site owner didn’t disable directory indexing. Let’s check it out:
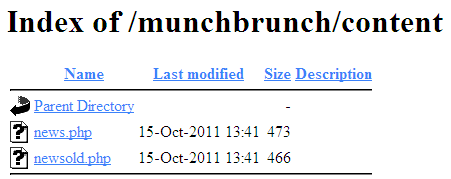
Nope, they definitely didn’t
The file newsold.php definitely looks suspicious. Let’s try our SQLi on newsold.php. This time, we find if we use the following line,
type=" or 1
, we get:

So, now that we know that this page is vulnerable to SQLi, we can extract data about the database with a UNION SELECT. First step is to figure out how many fields the current table has.
UNION SELECT 1,2,3 --
Results in a working page, showing us that there are 3 fields.
" UNION SELECT 0,0,table_name FROM information_schema.tables --
Tells us that there are two tables: users and news.
" UNION SELECT column_name,null FROM information_schema.columns WHERE table_name="users" --
Gives us the column names for users, and lastly:
" UNION SELECT 0,0,CONCAT(user,":",pass) FROM users --
Gives us the admin credentials, admin:GOTtalongPaSsWorDbecAUseIcAN. Log out, and relog into the admin account to get the key.