After reading through the Mandiant APT1 report detailing the presence of the Advanced Persistent Threat group 1 (APT1) which has been attacking a devastating number of companies and governments around the world a variety of questions come to mind. Considering the amount of time that has passed since Mandiant published the APT1 report in February one cannot help but wonder what the current status of APT1 is. As a quick overview for those who didn’t finish the report, Mandiant leaves us with two very profound statements regarding the composition of the APT1 group.

I’m definitely not one to make this distinction, and as such I will not be staging an argument one way or another here. However, I was left curious regarding the status of the group after so much time has gone by and further why some in the security industry reacted in such a poor manner towards the report being published.
APT1 - 3 Months Later
To begin discovering the current status of the APT1 group, one need do nothing more than some basic research concerning the topic. Currently there are a multitude of articles claiming that the APT1 group is back in action; which shouldn’t come as a surprise to anyone considering Mandiant’s CSO discussed APT1 resurfacing within a month of the report being published.
Essentially, any group operating for as long and as covertly as APT1 had been only to suddenly be exposed to the world as having their hands in the metaphorical cookie jar would scatter immediately. However, once the dust had settled, and it became apparent to APT1 that many of the previously vulnerable companies were still indeed open and susceptible to attack, why would they have stopped? It would be in their favor to simply modify their code to change the hashed signatures, register some new domain names to redirect to their C2 servers, and resume business as usual.
Regardless of their identity it’s painfully obvious that there’s massive profits in what they’re doing, albeit not necessarily monetary.
The Response of our Community
What I found most intriguing regarding the entirety of Mandiant releasing this report is not necessarily the content, but more the security communities response to its release. Initially, upon finishing the report, it would seem that what Mandiant has done is give a leg up to information security companies everywhere in the defenses against APT1. Yet, for some reason, many feel that Mandiant had various, potentially misplaced, motivations for publishing the paper, e.g. marketing or that the research done might have been shoddy and inaccurate.
Regardless of one’s stance on these claims, I feel them all to be largely unfocused. This report was very well put together as it is comprised of roughly 55 pages of nothing but data and evidence regarding APT1’s movements, followed by 2 pages offering 2 powerful possibilities. The entirety of cyber security professionals should all at least agree that the APT1 group poses a substantial threat to not just the United States, but the entire online world as Mandiant’s map below also suggests.
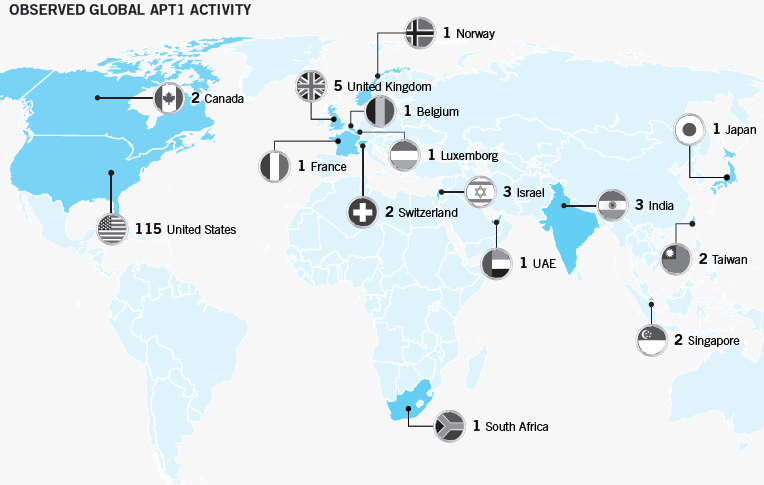
Mandiant publishing this information detailing the specifics of how this group moved and what their motivations were should truly be the takeaway of the report, as opposed to any assumptions about what Mandiant might have been implying. Furthermore, Mandiant wasn’t the only entity which suggested APT1’s Chinese origins as the APT1 malware samples are were available online for one to perform one’s own forensic analysis. (As of October these malware samples seem difficult to get ahold of)
Concluding Thoughts
In short, the true question likely being explored by Mandiant among other companies at this moment isn’t regarding whether or not APT1 is back, but to what extent are they back. It seems clear that APT1 has done relatively little to cover their tracks in this second go around of attacks, and even in the first, but is this simply a guise to draw attention away from other, potentially more devastating, APT1 actions.
It is because of these higher tier threats that I find myself excited to be where I am today. Having just been accepted to NYU-Poly’s Masters of Cyber Security program, and managed my way into Brooklynt Overflow, it is these types of threats that I am eager to tackle going into the future.
Regardless of the Chinese government’s involvement in these types of groups, it remains clear that the United States possess an array of companies and federal entities ready to combat these types of threats online, and it is because of this I feel that continued openness of research regarding malicious entities to be admirable and something we should all strive for.