Brooklynt Overflow recently participated in Olympic CTF finishing in 29th place. This is a write up of the aski challenge.
The aski program is a large stripped statically compiled 32 bit elf binary that opens a window and plays a video of a skier performing a trial as a series of ASCII symbols.
I suspected that the key was embedded in one of the frames because each frame goes by so quickly. The first thing I did was try grepping for the key, but no luck. I did however find many references to the INFLATE and DEFLATE algorithms (part of zlib), ssl and what I suspect to be AAlib although I didn’t find a copyright string. So, best case scenario there is some compressed ASCII that contains the flag, worst case scenario there is encrypted compressed AA formatted data that gets drawn to the screen. Great, I changed my strategy and looked for the routines responsible for drawing the frames to the window.
I discovered that the function at 0x804AB00 is responsible for opening the window and that the content of the video is played by the function at 0x804ABB0 both of which are called from main. The function 0x804ABB0 accepts two function pointers and a pointer to some data. I discovered that the pointer to data had the magic number for zlib compressed data. I dumped that memory and decompressed it again grepping for the flag but came up dry.
The second function pointer argument on the other hand was interesting. I discovered that by setting a breakpoint on the end of the longest code path I could single step through frames of the video.
Analyzing the video frame by frame I noticed that in the lower left the characters of the key were appearing every several frames. Below is the compilation of important frames.
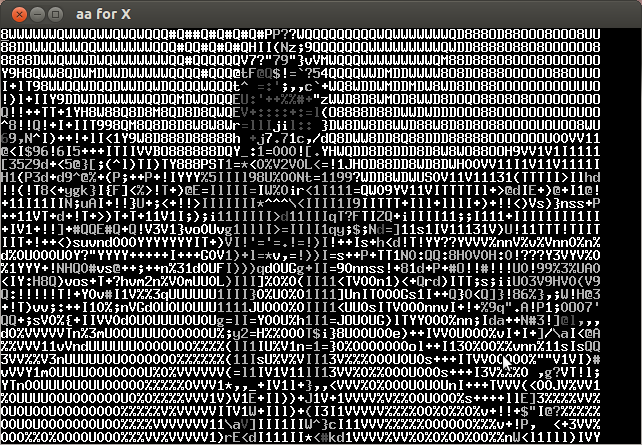
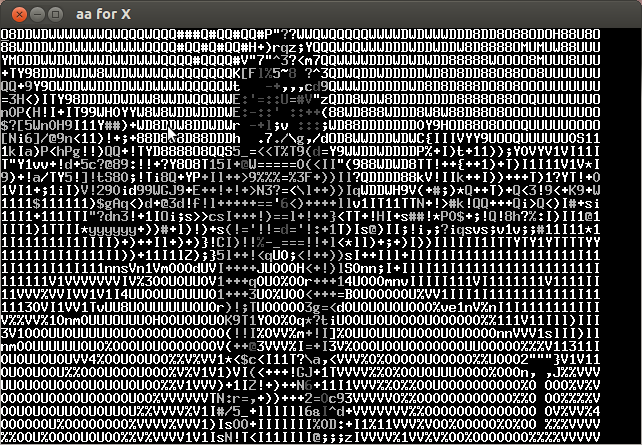
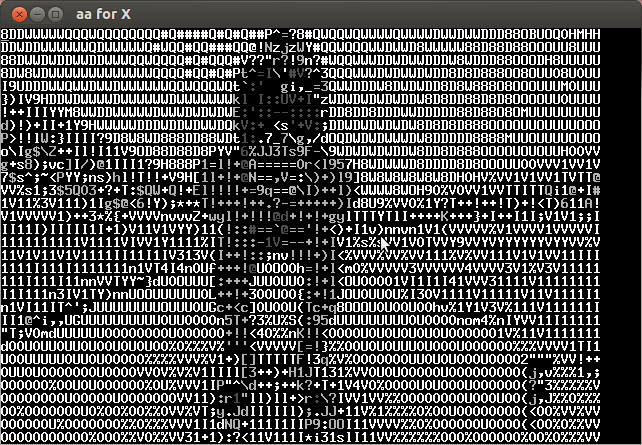
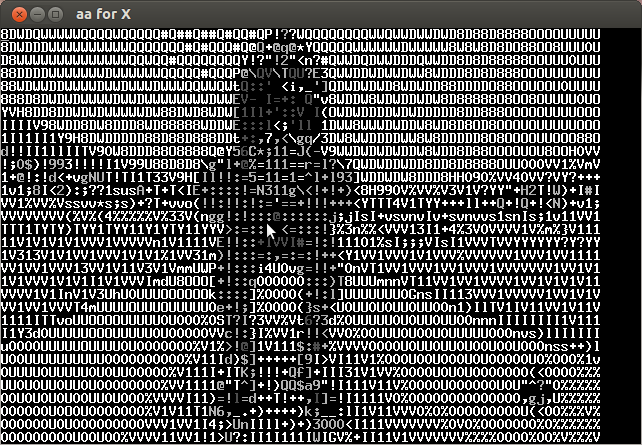
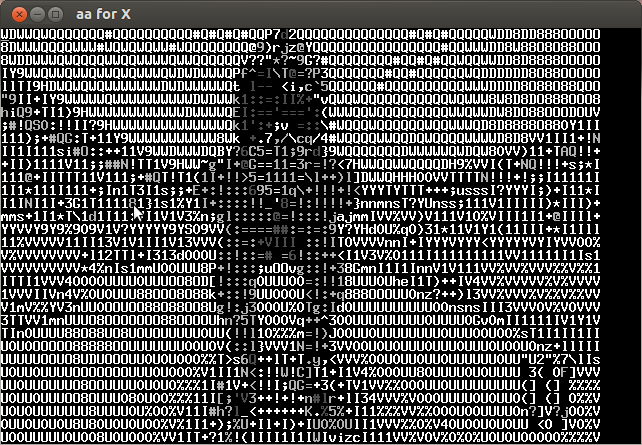
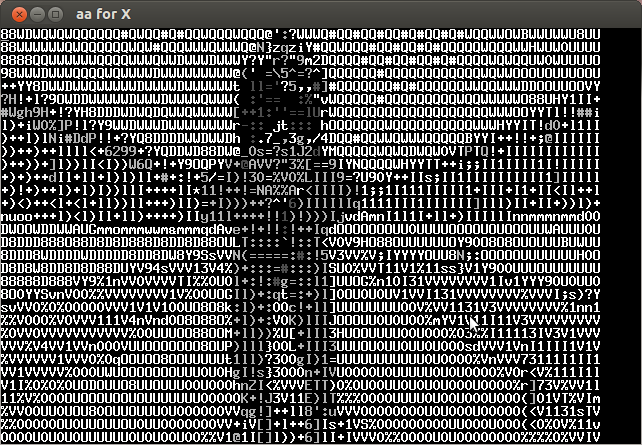
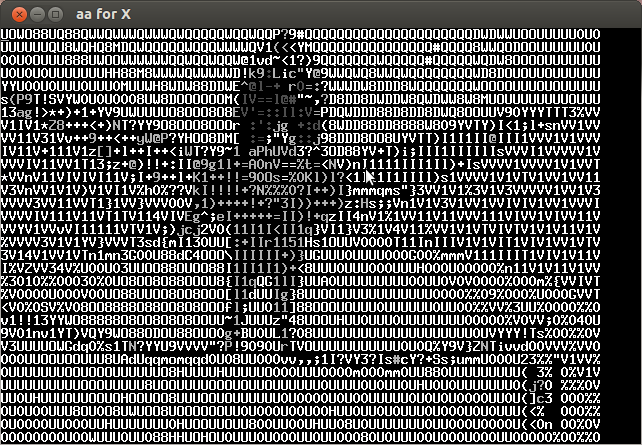
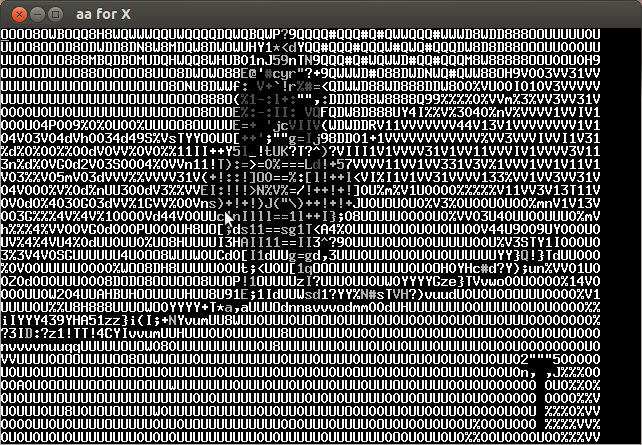
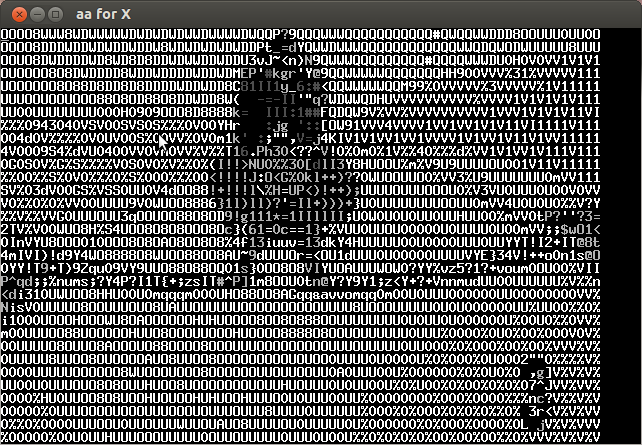
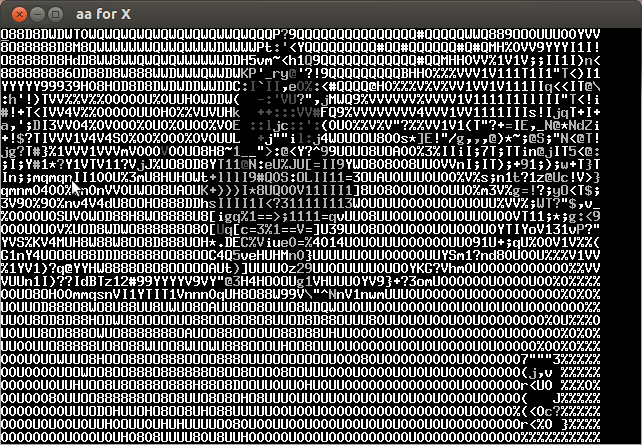
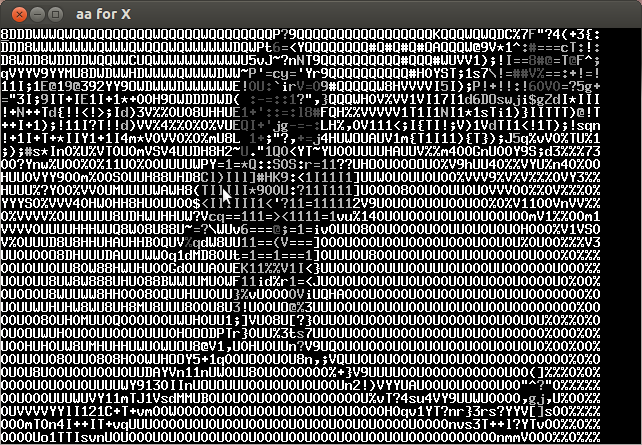
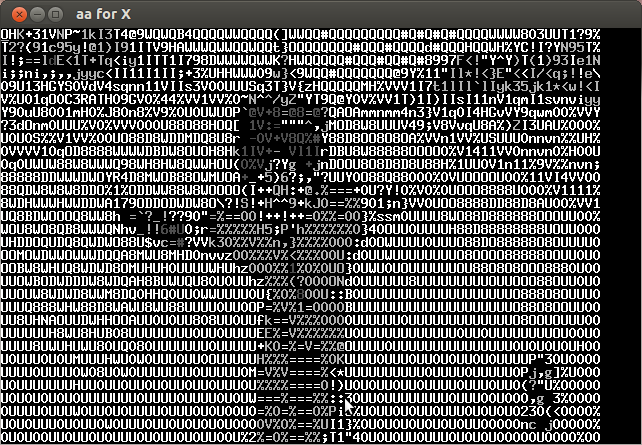
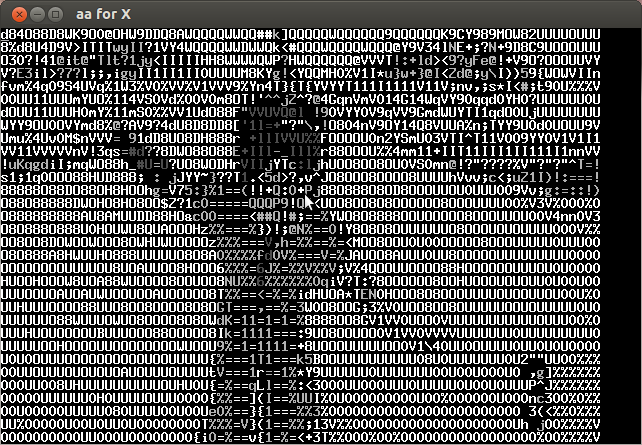
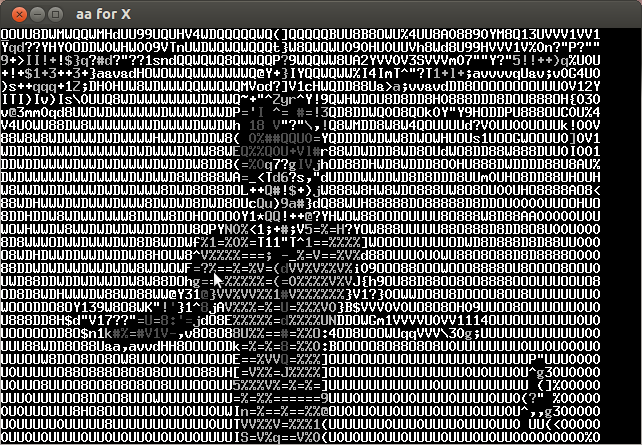
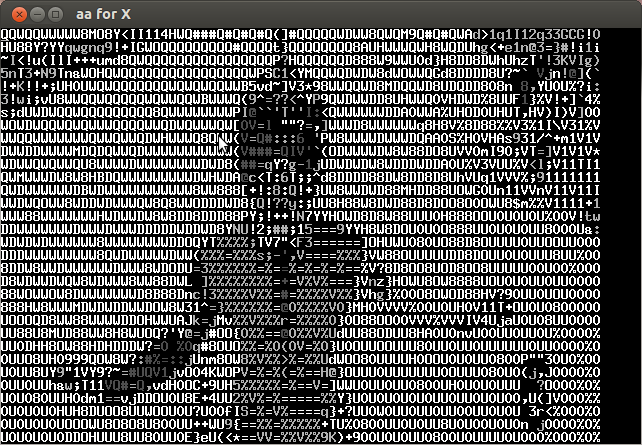
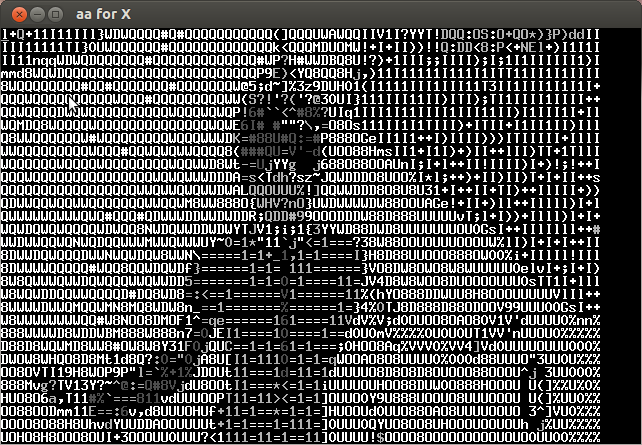
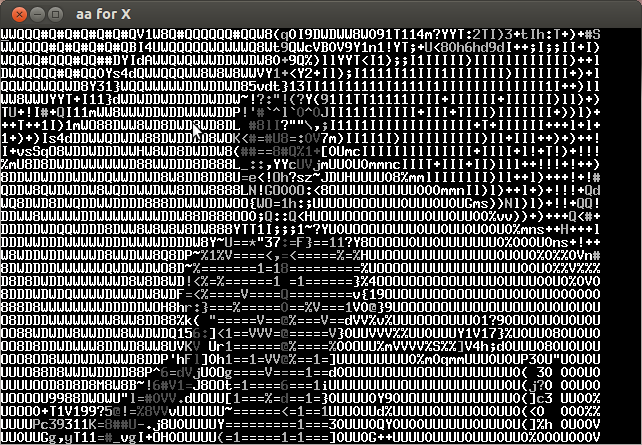
The key is CTF+WINT3R+S3A50N.
You can find the .gdbinit file with the breakpoints and the binary in the OSIRIS CTF-Solutuions repo on Github.